SHRM has partnered with Security Management Magazine to bring you relevant articles on key workplace topics and strategies.?
He may have been an original master of disguise. Benjamin Franklin Stringfellow was adept at changing his appearance to seem like a store assistant, a dental apprentice and even a woman going about her day, all while engaged in espionage for the 4th Virginia Cavalry during the U.S. Civil War in the 1860s.
A former Latin teacher in Mississippi, Stringfellow operated extensively in Washington, D.C., and Alexandria, Virginia, acquiring information that was ultimately passed to Confederate General Robert E. Lee to help the Confederacy win battles against the Union Army. His exploits also led to his capture. On the third such incident in April 1865, he escaped during a prison transfer and fled to Canada. He lived there until 1867, when he wanted to return to the United States to marry Emma Green—who had helped him pass on information about Union troop movements and strategies during the war.
As Stringfellow aged, he became an ordained Episcopal priest. He also wrote to former Union Army General and then-President Ulysses S. Grant, confessing that Stringfellow had once been close enough to shoot him in 1864 but refrained. Grant responded to the letter, thanking Stringfellow and committing that he—or any future U.S. president—would honor future requests Stringfellow made of them, according to the archives of the Office of the Director of National Intelligence.
“In a letter to President William McKinley in 1898, Stringfellow referenced Grant’s offer, and asked that he be allowed to serve as an army chaplain in the Spanish-American War,” according to the ODNI. “McKinley agreed.”
By all regards, maybe McKinley shouldn’t have. Stringfellow’s background was full of red flags: operating as a spy on behalf of rebels attempting to overthrow the U.S. government, marrying a former Confederate spy, engaging in a pattern of deception, breaking out of prison and fleeing from the country to remain beyond the reach of justice. But Stringfellow had changed. He had grown older. He no longer dressed up in disguises. He’d embarked on a new career path, with a family to support, and he appeared to have found a new cause to champion—providing ministry to those in need—in a possible change of heart.
At the same time, society at large had changed, too. There was a vast belief that individuals who had fought, served and aided the Confederate Army should not be persecuted after the end of the Civil War. And America, along with the world, was in the midst of the Second Industrial Revolution where society learned to embrace new risks from factories, power sources and modes of transportation.
What is and is not an acceptable risk changes over time. An unacceptable risk on one day—such as allowing a spy for your former enemy to serve in your ranks—might be acceptable 10 years on. Understanding how to weigh these risks while monitoring for new ones is a core aspect of the security clearance process for the U.S. government. That work has become more challenging as risk factors shift and people across all generations are increasingly globally interconnected.
“Technology underpins a lot of these changes,” says Marek N. Posard, military sociologist and professor at the Pardee RAND Graduate School. “It’s not even an age-based thing. Younger people just tend to be an earlier adopter of technology. But technology is the driving force.”
The Foundation
Following a U.S. Supreme Court decision in 1959 that said federal contractors had a right to due process when their security clearances were revoked (Greene v. McElroy), U.S. President Dwight D. Eisenhower issued an executive order in 1960 to create a process that standardized the adjudication process for a security clearance.
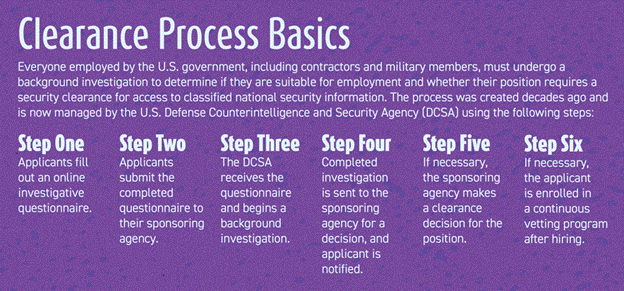
Sixty-two years later, that process remains largely unchanged. Applicants for U.S. government jobs, military roles or contract positions fill out a questionnaire, return it to their sponsoring agency, and a government department reviews the questionnaire and conducts a background investigation. After completing the investigation, the findings are sent to the sponsoring agency for a decision—called adjudication—and the applicant is notified of that decision.
If an agency hires an applicant, it also determines if he or she requires a security clearance to complete his or her work. If denied a position after the adjudication process, applicants have the right to appeal the decision and review the materials used in the background investigation. To do this work, adjudicators refer to a set of guidelines from the nation’s top spy—the director of national intelligence (DNI). James Clapper, who served as DNI from 2010 to 2017, issued the most recent guidelines, Security Executive Agent Directive-4 (SEAD-4), during the last year of his tenure.
“National security eligibility determinations take into account a person’s stability, trustworthiness, reliability, discretion, character, honesty and judgment,” according to the SEAD-4 guidelines. “No amount of oversight or security procedures can replace the self-discipline and integrity of an individual entrusted to protect the nation’s secrets or occupying a sensitive position. When a person’s life history shows evidence of unreliability or untrustworthiness, questions arise as to whether the individual can be relied upon and trusted to exercise the responsibility necessary for working in an environment where protecting the national security is paramount.”
Adjudicators evaluate applicants along 13 guidelines, including their allegiance to the United States, foreign influence and preferences, sexual behavior, financial considerations, alcohol and drug use, psychological conditions and use of information technology, in the context of the applicant as a whole person. This means that for each factor adjudicators should assess the nature, extent and seriousness of conduct; circumstances surrounding the conduct; age and maturity; motivations; and likelihood of continuation or recurrence of that conduct. Additionally, adjudicators must also consider if the applicant reported the information and was truthful and complete about doing so; demonstrated positive changes in behavior; and sought assistance and followed professional guidance where appropriate.
“Although adverse information concerning a single criterion may not be sufficient for an unfavorable eligibility determination, the individual may be found ineligible if available information reflects a recent or recurring pattern of questionable judgement, irresponsibility or unstable behavior,” the SEAD-4 said. “However, a single criterion may be sufficient to make an unfavorable eligibility determination even in the absence of a recent occurrence or a recurring pattern. Notwithstanding the whole-person concept, pursuit of further investigation may be terminated by an appropriate adjudicative agency in the face of reliable, significant, disqualifying, adverse information.”
Changing Roles
The robust process for adjudication and clearances takes some time, and it has not always been managed by the same agency. Before the mid-2010s, the U.S. Office of Personnel Management (OPM) played a major role in handling adjudication and background checks for non-intelligence community personnel.
After a massive data breach by the People’s Republic of China in 2015, OPM created the National Background Investigations Bureau to make its systems and processes more secure while also overseeing the background check process. Then, in 2019, the U.S. Department of Defense (DOD) announced that the NBIB would transition with the Defense Security Services into a new DOD agency—the U.S. Defense Counterintelligence and Security Agency (DCSA)—and an executive order tasked the agency with conducting all background investigations for the federal government.
This was done, in part, because of a significant backlog in the process, starting at 725,000 in 2018 and dropping to 410,000 in June 2019. It took nearly 150 days for a Top-Secret investigation and adjudication, according to a DOD press release.
That backlog is now under control, says Heather Green, assistant director of vetting risk operations for the DCSA, with a normal level of 171,000 cases in the inventory, individuals completing the Top-Secret process within 81 days, and others completing the non-critical sensitive process within 55 days, despite the challenges of the COVID-19 pandemic.
“We had to pivot pretty quickly in coming up with alternative solutions because it was an unprecedented time—especially at the beginning when people were in lockdown and limiting face-to-face interactions,” she says. “We worked closely with other agencies to work through alternative solutions on background investigations, looking at virtual opportunities to engage with subjects.”
DCSA has also been keeping another challenge in mind—future changes to the adjudication and risk evaluation process to keep up with the needs of the federal workforce and changes in risk tolerance across society.
Future Additions
How do you identify when societal change might happen and how those risks are shifting? That’s something the U.S. Security Clearance, Suitability and Credentialing Performance Accountability Council’s Program Management Office wanted to learn more about. So, it sponsored a study by RAND’s National Defense Research Institute to identify emerging patterns among younger generations amidst social changes. Researchers Marek Posard, Emily Ellinger, Jamie Ryan and Richard S. Girven then took the review a step further to look at the personnel vetting guidelines used for the adjudication and clearance process to determine who is eligible, who is deemed a risk and how social and generational changes might affect younger candidates’ ability to be hired into a sensitive position. They published their findings in 2021, including a brief on how social and generational changes have already impacted this process.
“For example, the adjudicative guidelines outlined by the Director of Central Intelligence in 1968—a precursor to the SEAD-4—once listed cohabitation and homosexual conduct as risk factors,” the researchers explained. “Because societal norms have changed since then, and expectations about what could be used by a foreign power to blackmail someone in a position of trust have also changed, those topics no longer exist in today’s SEAD-4.”
In their report, Posard and his fellow researchers looked at the guideline topics from the SEAD-4 and how they may need to adapt in response to broader social changes to recruit the workforce of the future.
“One thing that is important when looking at history is, is there a clear justification for why this is a risk factor?” Posard asks. Guidance from 1968 listed cohabitation and homosexuality as risk factors, but Posard notes: “Just because something was considered not acceptable in a prior time, was it a risk factor?”
For instance, the SEAD-4 guidelines include financial considerations because if an applicant has a large amount of debt, it could demonstrate poor self-control, poor judgment or an unwillingness to follow the rules. That applicant could also be a target for foreign nationals who promise payouts in exchange for classified information.
Recent guidance, however, suggests that financial status could be less of a concern for adjudicators now if the individual has shown a good faith effort to repay his or her debts or that they were unemployed or underemployed during the time the debt grew, such as during the Great Recession or the COVID-19 pandemic.
Financial risk factors may need to be revisited in the future because it is now more common for individuals to carry significant amounts of student loan debt and experiment with new currency and investment models, such as cryptocurrency. And as people grow older, they take on new forms of debt that are generally considered an acceptable risk.
“When you’re younger, you might have student loan debt. But as you age, as you get married and have children, you see those debts increase in other ways—credit card debt and mortgage debt,” Posard says. “As a result, you want to make sure people are managing those debt loads accordingly.”
SEAD-4 also considers foreign nationals and allegiance to the United States as part of the adjudication process for applicants. While this makes sense because it could create opportunities for recruitment by foreign intelligence services, it also poses a challenge because globalization, Internet access and ease of travel have “reduced barriers” to contact with foreign nationals, the researchers explained. Increased numbers of foreign-born individuals in the United States and participants in study abroad programs have also changed this risk.
“We note that some national security positions requiring a security clearance require a deep understanding of local cultures and languages that typically come from firsthand experiences,” the researchers wrote. “In these cases, the personnel vetting guidelines may hinder recruitment and retention of people with these mission-critical skills. Thus, a balance between these two needs (security and personnel with mission-critical skills) may require adjustments in future contexts.”
Another potential point of contention could be drug use. Nineteen U.S. states, Guam, the Northern Mariana Islands and Washington, D.C., have legalized adult use of marijuana for recreational purposes. Thirty-eight U.S. states, Guam, the Northern Mariana Islands, Puerto Rico, Washington, D.C., and the Virgin Islands have also legalized medical marijuana. The drug, however, remains illegal at the federal level. This means that many people, including those just entering the workforce, are using marijuana. In 2016, 33 percent of Americans ages 18 to 25 self-reported that they used marijuana in the past year, according to the RAND researchers’ review of National Institute of Drug Abuse data.
“The various state laws on marijuana use create opportunities for applicants to violate federal laws—either knowingly or unknowingly,” the researchers explained. “These various laws may affect recruitment of young people by dissuading potential candidates from considering positions that require a security clearance.”
In addition to marijuana use, the researchers wrote that the risks of dependency were far higher for nonprescription psychotherapeutics—pain relievers, tranquilizers, stimulants and sedatives—that were the second most used illicit drug by Americans between the ages of 18 and 25. For adjudicators, it must be a constant assessment of risk associated with drug use or relationships with individuals who might have a substance abuse problem, such as a relative with an opioid addiction.
“The opioid crisis is real, and it’s an area that is a risk factor and where people might feel like they have no chance of getting a clearance because they’re associated with someone or they might have their own issues, as well,” Posard says.
Nowhere is societal and generational change more notable, however, than online. Researchers noted that guidelines around digital personal conduct and how applicants use information technology will need to be revisited. All generations today engage in social media use, sharing vast amounts of personal data with others via the Internet. This could pose a significant risk factor.
“We found that the vast majority of younger adults are the most active on social media and how much information they share online appears to be on the rise,” the researchers wrote. “Although younger adults report more vigilance in data privacy than older adults, we found there is still a noticeable percentage of the former who are less concerned about what they share online.”
And social media is not the only factor. The growth of the Internet has also created new avenues for crime and for individuals to engage in illicit activities.
“All those risk factors—foreign contacts, issues related to buying drugs, allegiance—that carries over and can be done online,” Posard explains. “In the past, if you were a foreign intelligence service and you wanted to recruit an asset in the United States, you might have to send someone to the U.S. You can do that virtually now, through LinkedIn, through video, through the metaverse. I think this idea that there’s a digital world and a real world is changing before our eyes, and that’s only going to create more risks—or expand the scope of the risk we’re looking at.”
To address some of these risk factors in response to generational changes, the researchers made several recommendations for the U.S. federal government to consider, along with being transparent with applicants about the guidelines used by adjudicators in determining eligibility and security clearance decisions. The recommendations included revising the language on risk factors related to student loan debt to address how applicants are managing essential debts instead of satisfying them. The researchers also suggested changing the guidelines that focus on foreign nationals to focus on the “nature of contacts” and the “risk levels of their home countries,” such as placing a greater emphasis on countries determined to be a higher threat in the ODNI’s yearly worldwide threat assessment.
Additionally, the researchers recommended considering the legality of substances—such as marijuana—at the local and state level as a mitigating factor; placing student debt from an accredited institution as a lower risk factor than other forms of debt; adding a new guideline on personal conduct for online behavior; and that the federal government continuously reassess risk factors based on the outlined trends.
Since publishing their findings, Posard says the report has been circulated throughout parts of the federal government. The U.S. Senate Intelligence Committee also approved legislation that would prevent national security agencies from removing applicants who have previously used marijuana from consideration for positions.
“I am pleased that this year’s bill drives serious improvement to the IC’s hiring and security clearance processes, so that the IC can attract and expeditiously on-board a talented, diverse, and trusted workforce,” said U.S. Senator Mark Warner (D-VA), chair of the Senate Intelligence Committee, in a statement.
And Trusted Workforce 2.0—a whole of government background investigation reform effort that launched in 2018—may have adopted some of the researchers’ recommendations.
“The worst you can do is say it’s a risk factor because it’s always been a risk factor,” Posard says. “It’s an equality issue, too. I’m a sociologist, so my mind is always going to ‘who is this impacting?’ You need to look at the risk factor itself and see if there is a clear justification associated with that risk…it is piecing together data sources and making a qualitative assessment in the process.”
Continuous Vetting
Assessing the risk associated with applicants, current employees and clearance holders has traditionally been a formal process. Risk information is provided during the application period, or every five or 10 years after hiring—depending on the sensitivity level of the position.
Trusted Workforce 2.0 is looking to change that by creating a system that protects the workforce—and the agencies it serves—in real time by continuously vetting individuals. By October 2023, DCSA will have a system in place to conduct this process, which will run an automated record check to pull data from criminal, terrorism and financial databases, as well as public records, during individual’s period of eligibility.
If DCSA receives an alert—such as a recent arrest warrant for a clearance holder—it will then assess if the alert is valid and worth additional investigation and follow-up actions, such as suspending or revoking clearances. As of May 2022, 4 million military and contractor personnel were enrolled in the continuous vetting system comprised of three high-value automated checks, Green confirms. The DCSA was also on pace to transition the entire system to include seven automated checks.
“The goal is to mitigate some of those personnel situations before they become a problem,” Green says. “We work with the individual to mitigate those issues. Their clearance may be affected, depending on how significant the issue is.” The other goal is to ensure that the process is not stagnant, and that DCSA continues to evaluate what it’s doing and how it needs to evolve as the environment around it changes.
“As we continue to learn and as societal norms change, we always have to have an eye on what’s happening, what trends are we seeing and where we need to make adjustments to our processes and our procedures,” she adds.
This includes assessing if—and how—online activity through social media should play into the investigative and adjudication process.
“Social media is definitely something we’re continuing to explore,” Green says. “It is something from a policy perspective that we’re continuing to look at the value of and the automation needed to add social media or publicly available electronic information into the program as a whole.”
“Social media is tricky, though, because there is a lot of information out there,” she adds. “We want to make sure we’re focused on what we need to know and value added. That is something the department and the federal enterprise is exploring on how we would manage social media moving forward.”
Megan Gates is senior editor at Security Management. Connect with her at megan.gates@asisonline.org. Follow her on Twitter: @mgngates.
This article is adapted from Security Management Magazine with permission from ASIS © 2022. All rights reserved.